Data security is one of the most critical issues in data storage, and data encryption is a leading method of data protection. By encrypting the data stored on a drive, you ensure the data remain secure even if the user loses physical control of the storage device. The encrypted data can only be unlocked and deciphered once you deliver the proper credentials.
AES
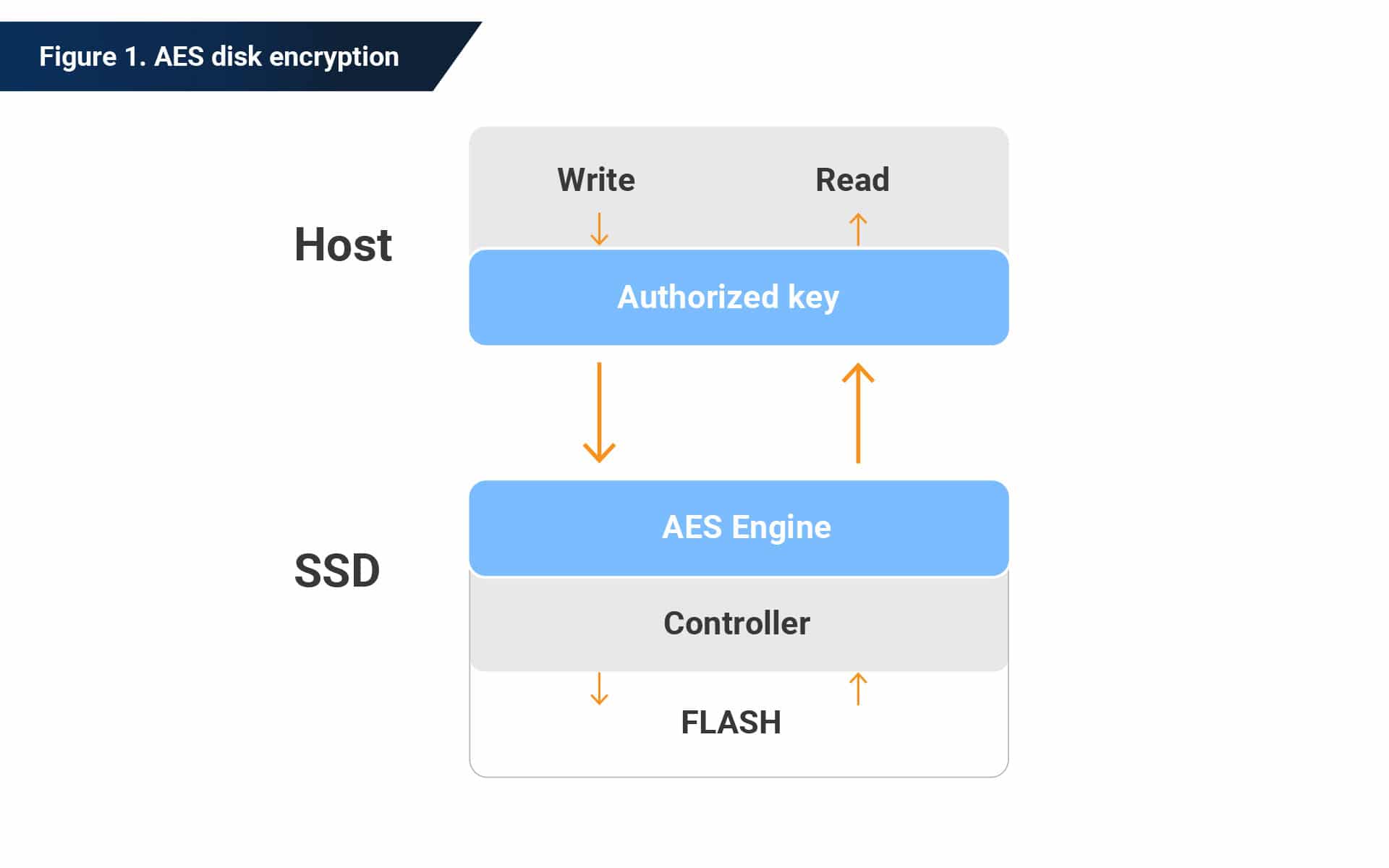
SSDs use an AES algorithm with symmetrical encryption keys.
The first is the encryption key used to encrypt all data stored on the SSD. If the SSD uses AES 256-bit encryption, this key is a 256-bit number generated randomly and stored in an encrypted format on a hidden area of the SSD. The encryption key never leaves the SSD and is known only by the SSD itself.
The second key is the authorization key. This is set by the user, and it controls access to the SSD. If you don’t set an authorization key when you first use a drive, the SSD will appear to behave just like an unencrypted SSD. The data is still encrypted, but without a defined authorization key, the drive automatically decrypts read requests with the encryption key. Like the encryption key, the authorization key is never stored as plaintext. It is only stored in an encrypted state.
TCG OPAL 2.0, Opalite and Pyrite
Trusted Computing Group (TCG) provides a scalable infrastructure for managing encryption of user data in a storage device. It includes extensible features. With TCG, you can manage access control to user data stored on the storage device, including control of media encryption, Key Management, and Read/Write Lock State.
The “TCG Storage Security Subsystem Class: Opal”, also called “Opal SSC” or just “Opal”, is an implementation profile for storage devices that incorporates this functionality.
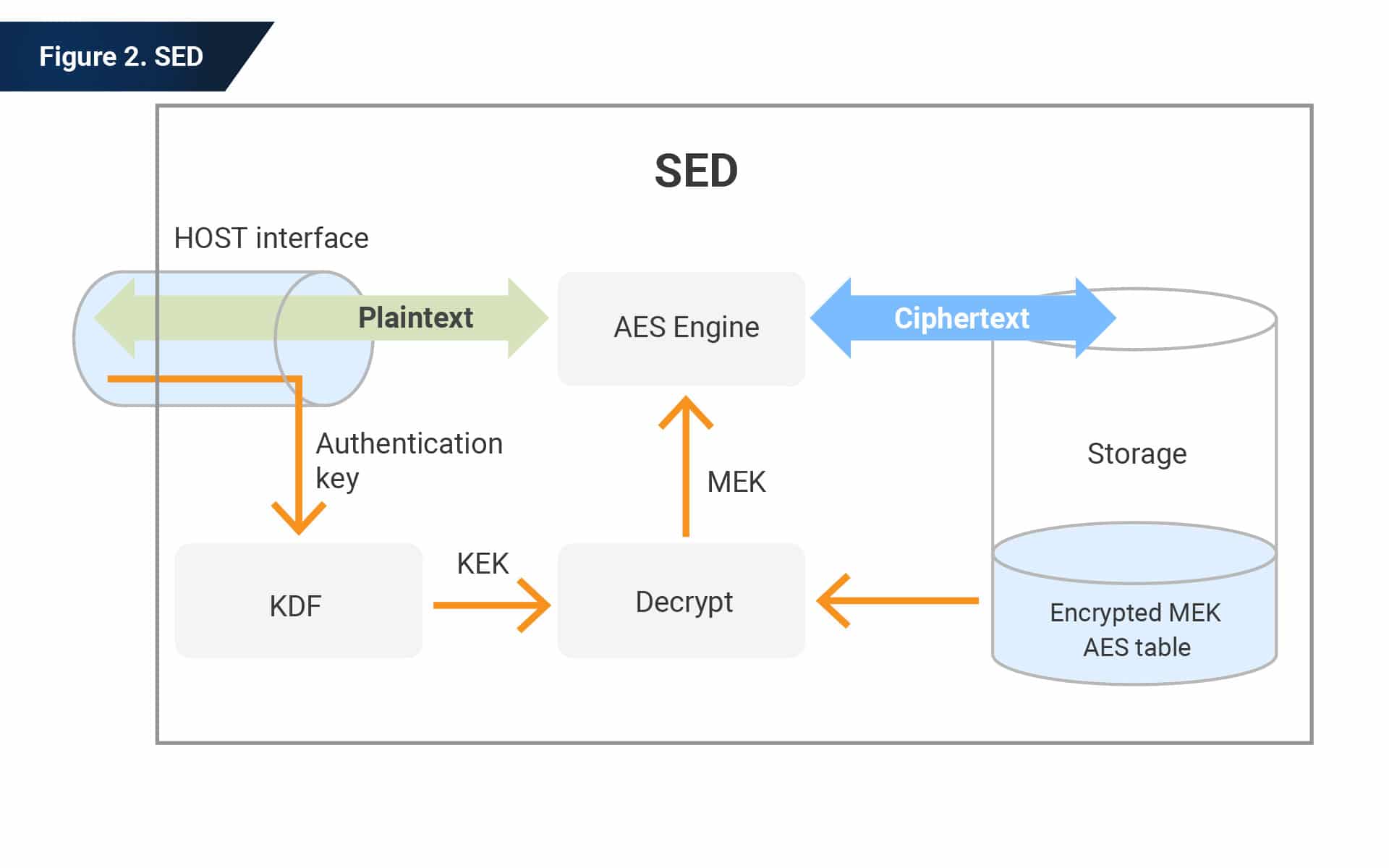
This example shows a Self-Encrypting Drive (SED)–a storage device that integrates encryption of user data. All data is encrypted when written and then decrypted when read. The drive encrypts and decrypts your data using a Media Encryption Key (MEK) generated internally in the Storage Device.
Opal provides a mechanism by which a host application that manages the Opal functionality in the Storage Device sets an authentication credential (i.e., a password) to enable access control to the user data. The OPAL 2.0 specification accommodates block sizes appropriate for SSDs and LBA range alignment to minimize write amplification.
For this reason, encrypted SSDs should be OPAL 2.0-compliant for optimal performance. They also need to be used with software that supports OPAL 2.0 since the specification is not backward-compatible.
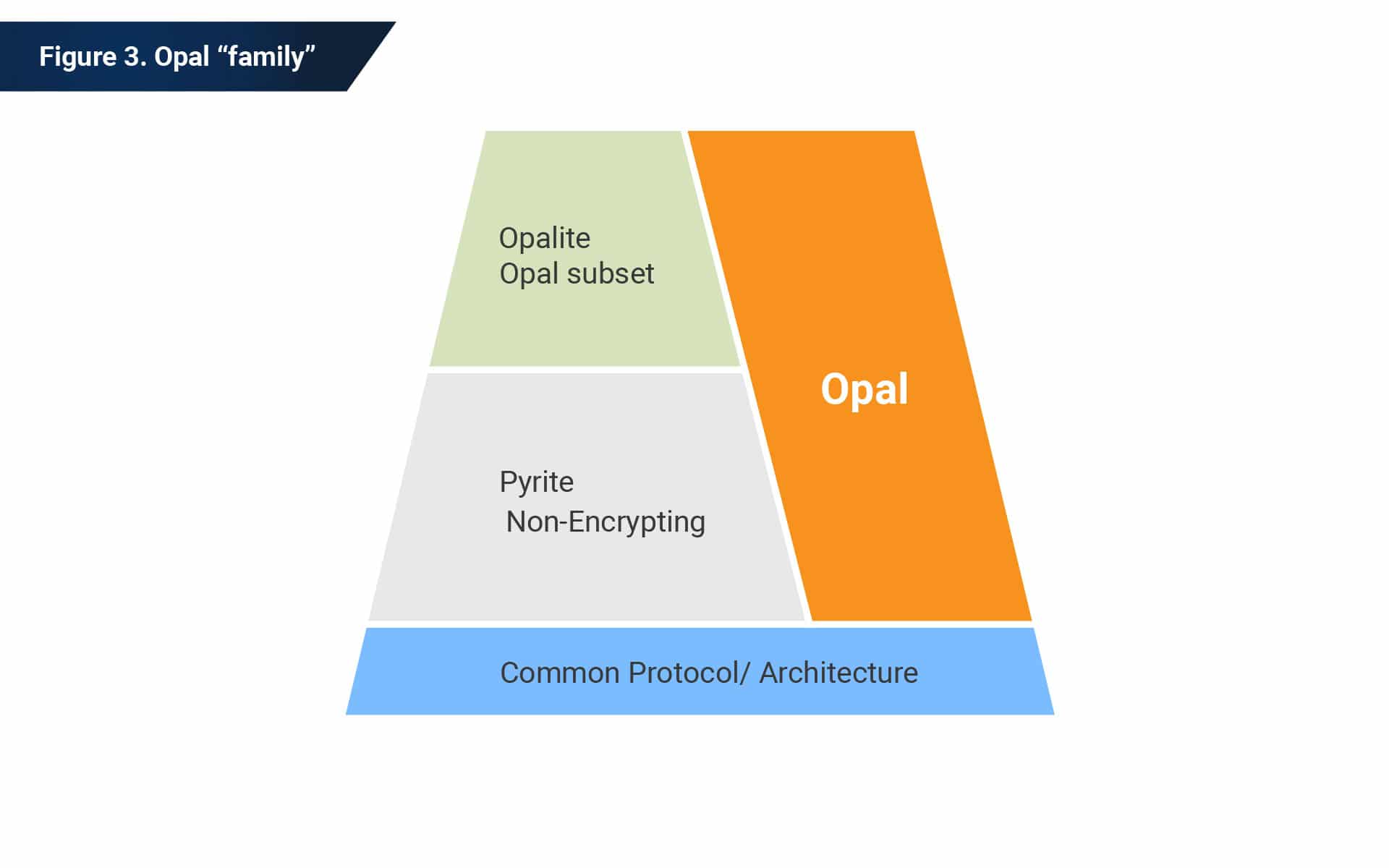
There are two new specifications in response to a request from the NVMe workgroup: Opalite and Pyrite. These two specifications are a subset of Opal. The primary difference between Opal and Opalite is that Opalite defines a single, global locking range, whereas Opal defines several configurable locking ranges. Opalite limits the number of supported users to two.
Pyrite is almost identical to Opalite, with one primary difference: Pyrite does not specify capabilities for cryptographic protection of data at rest. That means Pyrite does not support capabilities related to encryption and cryptographic erasure.
SHA and RSA
An SSD’s firmware is the code set that controls an SSD. Developers code firmware in much the same way as they code software. Software compilation has traditionally been considered a one-way operation. However, it is theoretically possible for a hacker to reverse-engineer a binary file to extract the source code. So, firmware developers need to identify when the firmware has been tampered with and prevent malicious firmware from being installed on a storage device. Generally, manufacturers use digital signatures for firmware upgrading, which means that digital signatures are essential for securing storage devices.
The RSA cryptosystem creates, manages, and secures digital signatures. When a program runs in an OS, the OS reads and displays that signature, and the user can verify that the software comes from a trusted vendor.
The digital signature also ensures that the firmware has not been tampered with and isn’t counterfeit. You can secure the firmware update process with a digital signature. Every drive interface, including SATA and NVMe, has a defined command sequence that sends a new binary code to a storage drive. This tells the drive to replace the current firmware. To ensure this command does not deliver incorrect firmware, the drive checks the target firmware for the correct model and type.
Securing data stored on SSDs
Ensuring the security of user data and protecting the integrity of SSD firmware against attacks is a top priority for every SSD manufacturer. The safest data storage devices include full encryption of user data, but data security is still of the utmost importance even without encryption. So, both encrypted and non-encrypted SSDs have features that protect the integrity of the SSD firmware, providing added protection of user data.