Over the past decade, solid-state disks (SSDs) have gradually taken the place of hard drives in many devices. More and more consumers and clients choose SSDs as their storage solution for notebooks, personal computers, and enterprise applications. As such, the need for SSDs to be reliable and secure is becoming more critical. The last thing anyone wants is for a faulty or aging SSD to be responsible for the loss of anyone’s crucial data. It’s necessary to monitor the health of SSDs and analyze an SSDs status to reassure a user that an SSD is still reliable and inform users when the life of an SSD is coming to an end.
The standard SSD lifetime and workload analysis tool is S.M.A.R.T. (Self-Monitoring, Analysis, and Reporting Technology.) This tool records drive status attributes, including erase count, bad block count, uncorrectable error count, CRC error count, SSD life remaining, and more. More advanced analysis tools, such as protocol analyzer, UART mode, and drive log, help for debugging and protocol trace analysis when an SSD encounters unexpected errors that are hard to resolve immediately. In some cases, using drive log to clarify issues is simpler and more efficient than using protocol analyzer and UART. It can save an engineer time by not going back and forth between two places, allowing the engineer to focus on drive log analysis to resolve any issue quickly. Therefore, it made sense to Phison to create a drive log as a helpful debug tool, enabling our customers to be more confident in Phison’s after-sales service.
The structure of drive log
Drive log saves in the data buffer. Once the host issues a vendor-specific command, such as a FLUSH command or idle, the drive log flushes into NAND flash to the SSD.
Drive log is comprised of three parts:
• Public area: Records general and public events.
• Private area: Records confidential events.
• Non-overwrite area: Records events that, once recorded, can’t be overwritten even when the public and private areas are full.
Record information for host, FTL, and Flash IP save in drive log. The information stores the data by unique key words:
• error event
• reset event
• abort event
• system event
The record information in FTL has a different variable to log for assert events and other error events. As for the record information of Flash IP, the program error, erase error, and read retry in fail CE, block, and page.
Encryption and decryption of drive log
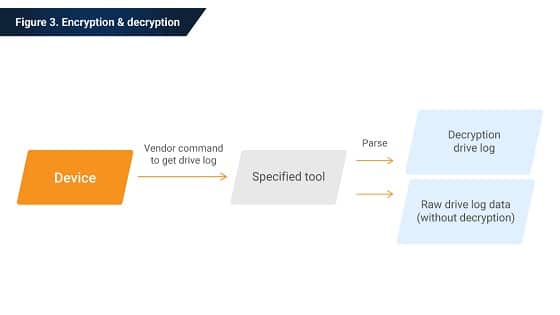
There’s one vendor command to get the drive log and encrypt the log at the same time.
After loading an encrypted log into the specific tool, the tool generates two files. One is raw drive log data without decryption, and another is decrypted drive log data. Next, the log data separates by the specific tool according to different requirements, which then displays event information to help an engineer analyze drive behavior and resolve problems.
Phison’s drive log give customers peace of mind
Phison has always offered a total SSD solution and services for customers. With the use of drive log, the processing time of RMA is reduced, and customer satisfaction is increased. Drive log is set to become the standard analysis tool in Phison SSDs.