Solid-state drives (SSDs) are used in laptops and PCs because they deliver significant performance boosts, enhance physical durability, and provide cost-effective price performance. As new SSD technology is released, businesses periodically replace and upgrade their PCs. But leaving data on repurposed drives is a significant security concern because using the operating system-based “delete” file or folder functions doesn’t permanently erase stored data. Even a “format drive” does not completely erase data. Secure erase is an effective way to remove data and protect the confidential data stored on repurposed drives.
Flash memory cell scheme
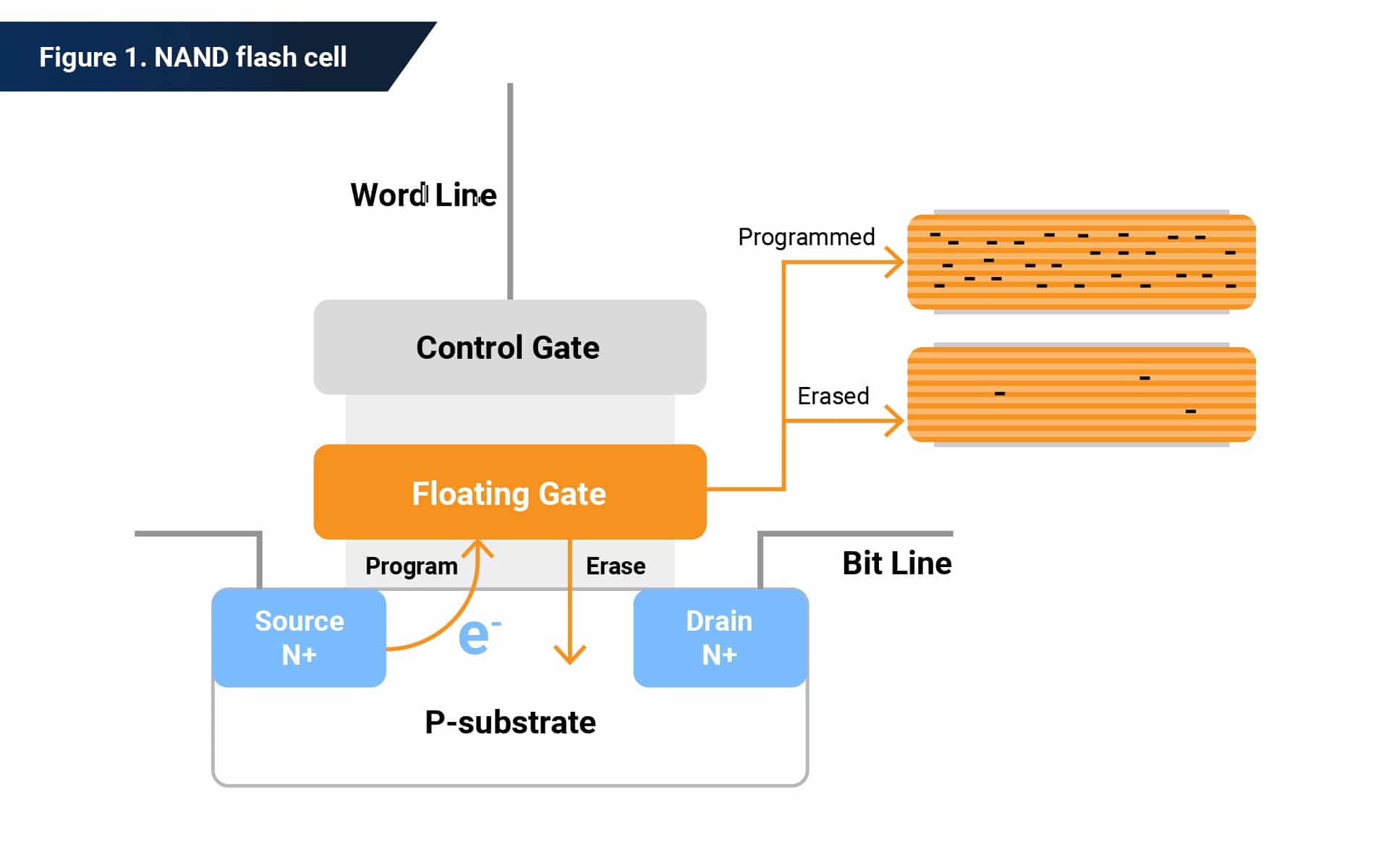
SSDs use NAND flash technology for data storage
A NAND flash cell uses a process known as Fowler-Nordheim tunneling to change the charge inside the floating gate. Writing (or programming) a “0” into a cell causes the accumulation of negative charges in the floating gate. Writing a “1” into a cell does not change the cell’s content. To change the content of a cell from “0” to “1,” the cell must be erased to release the negative charges in the floating gate.
The areas of an SSD where data is stored
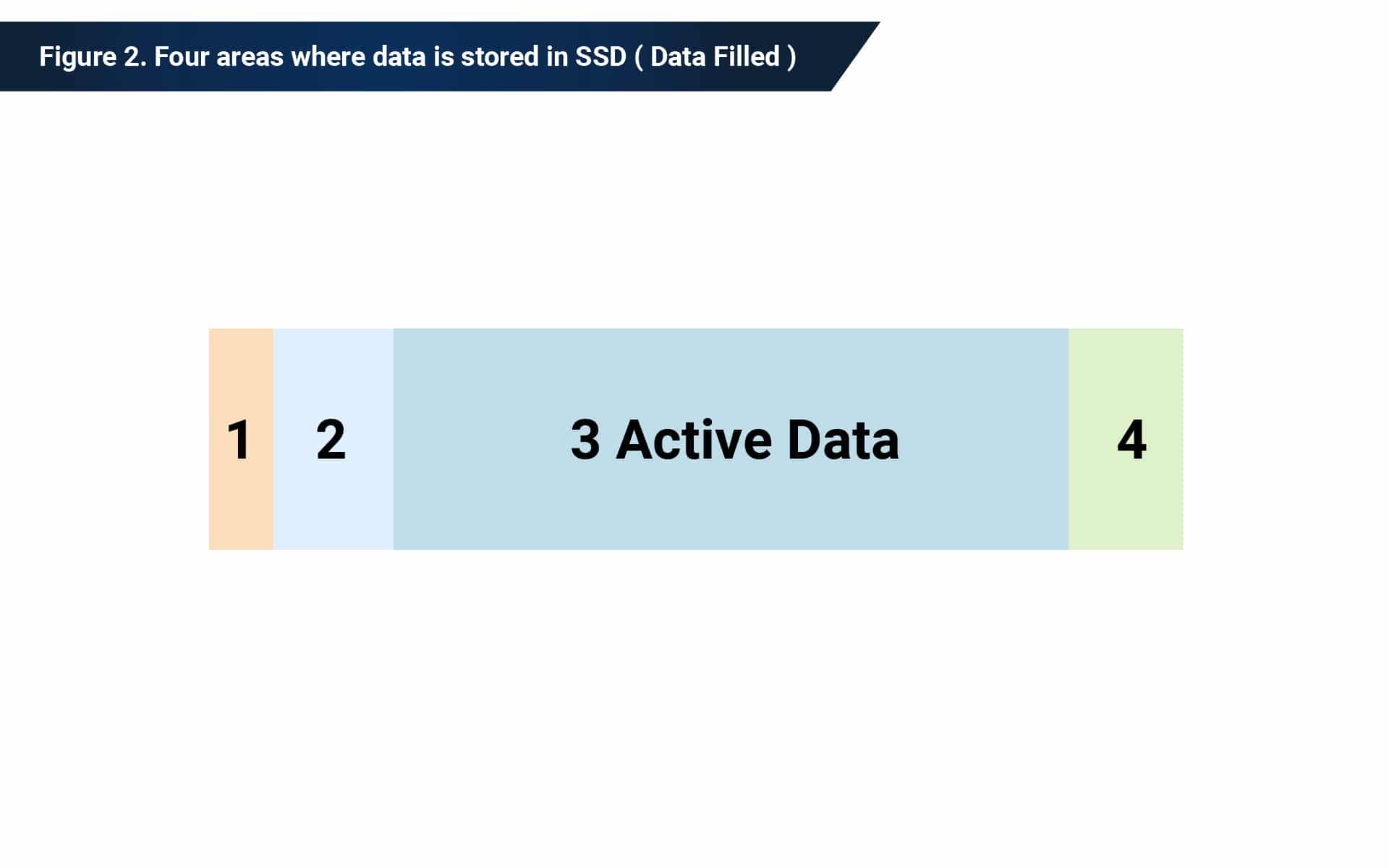
SSDs have four main areas where data is stored
- System area blocks, such as firmware, are generally stored in the first few blocks but can be located anywhere. No user data is stored in this area.
- Spare blocks can be stored anywhere. Old copies of user data are stored here until the garbage collection routine erases them during idle time.
- Active data is stored anywhere. Current user data is stored here.
- Retired blocks are blocks that are too damaged to use. Old copies of user data can be stored here.
What is secure erase?
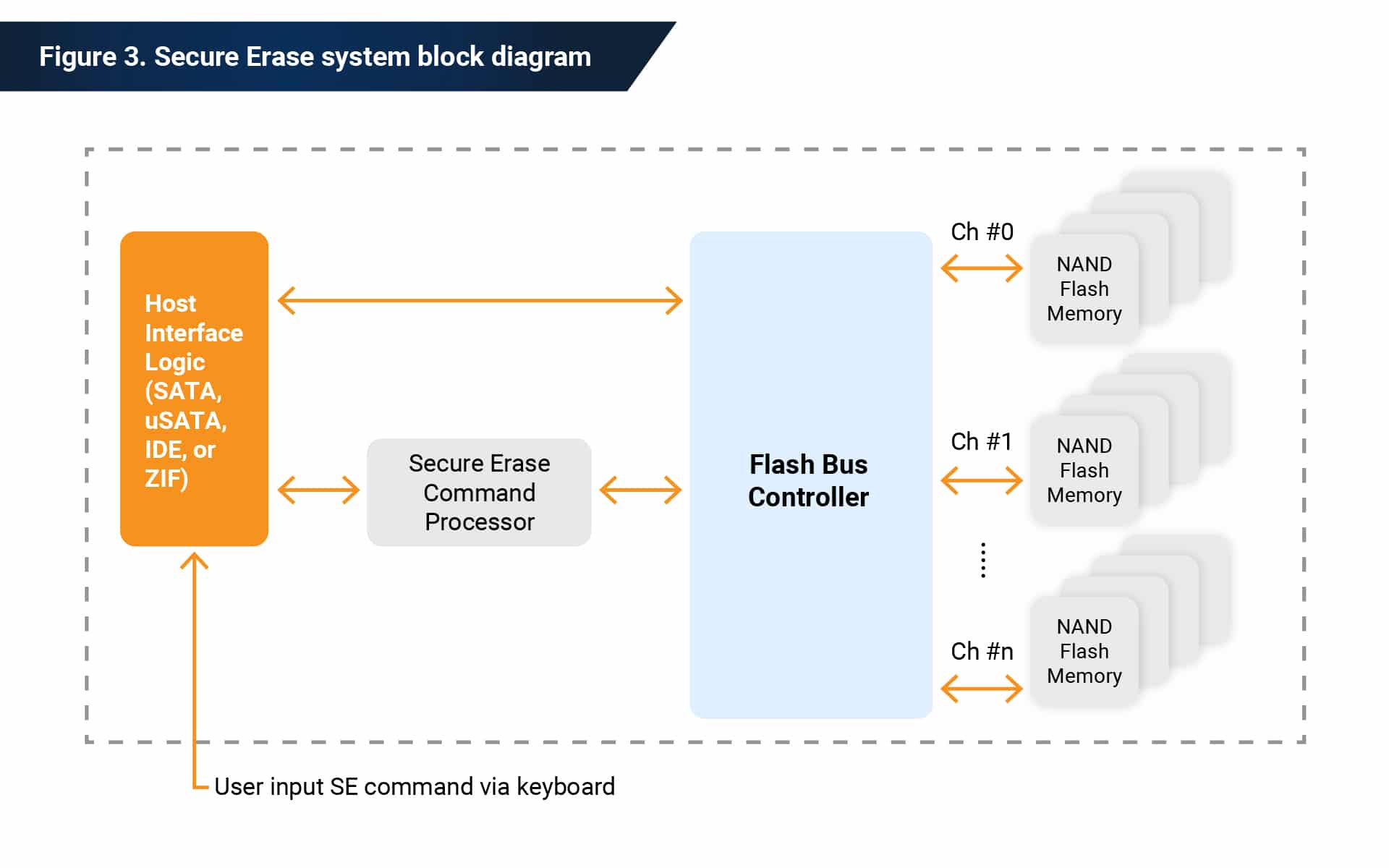
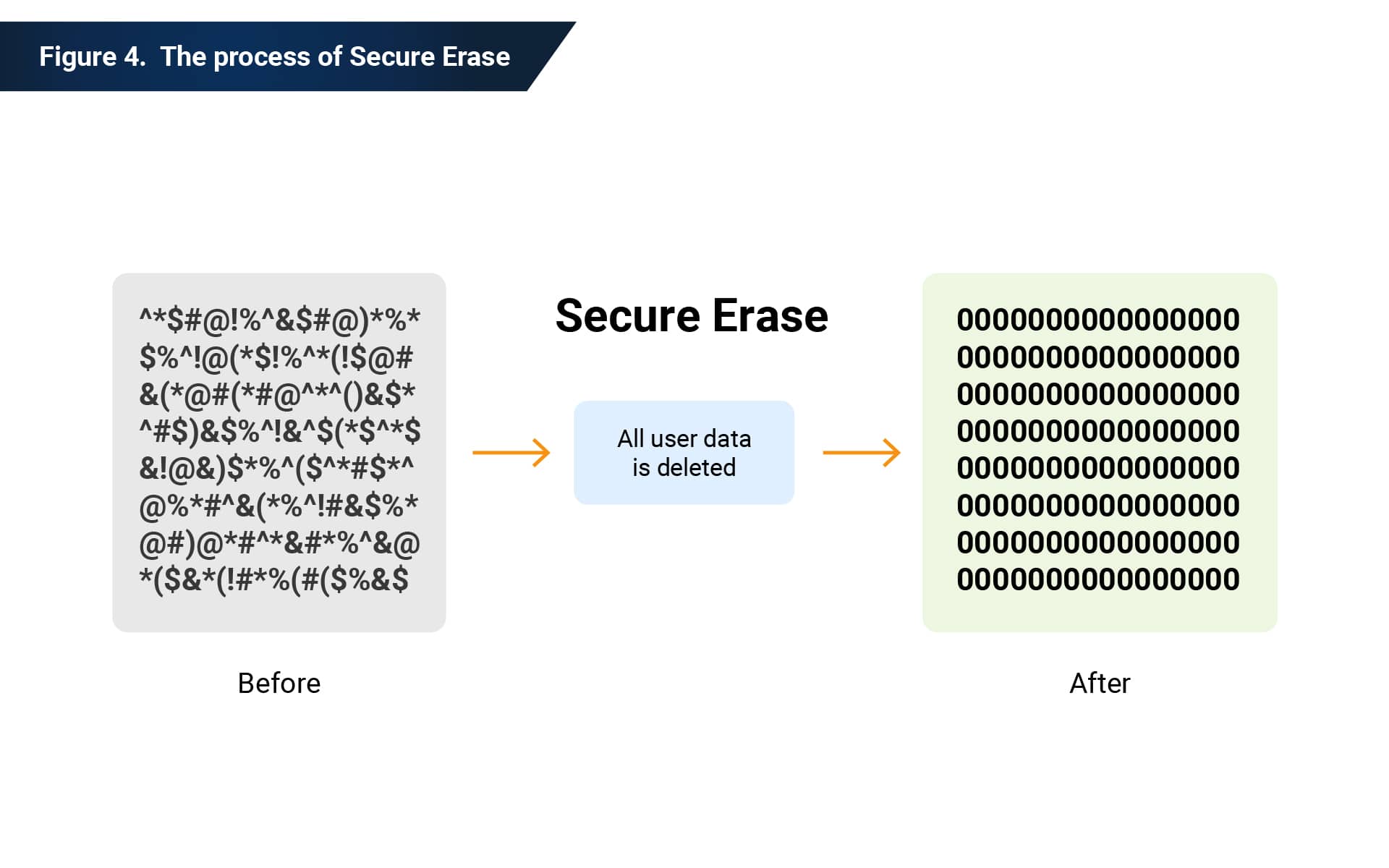
Secure erase describes the operation of entirely and irretrievably deleting user data from a storage device for privacy, confidentiality, and security reasons. Secure erase is a data erase method supported by the SSD controller that removes stored data from the drive’s flash cells.
Secure erase is an irreversible process. Once you perform a secure erase on a drive, the erased content is unrecoverable. You can initiate secure erase through a standard ATA Security Erase command to a drive’s controller using the drive’s IO interface. The command overwrites the NAND blocks of the drive (in-use and spare) with zeros.
When deleting data using secure erase, the tool erases the LBA (Logical Block Address) mapping table, active data, OS, and partition. Secure erase removes data included in areas 2, 3, and 4 (as shown in Figure 2) but does not touch system area blocks (as shown below in Figure 5, block #1).
If secure erase is interrupted by an unexpected power cut, the process will restart on the next SSD power-on state. Secure erase deletes all data and returns an SSD to a factory default state. This command is useful when running performance and benchmark tests.
Using secure erase with Phison SSD products
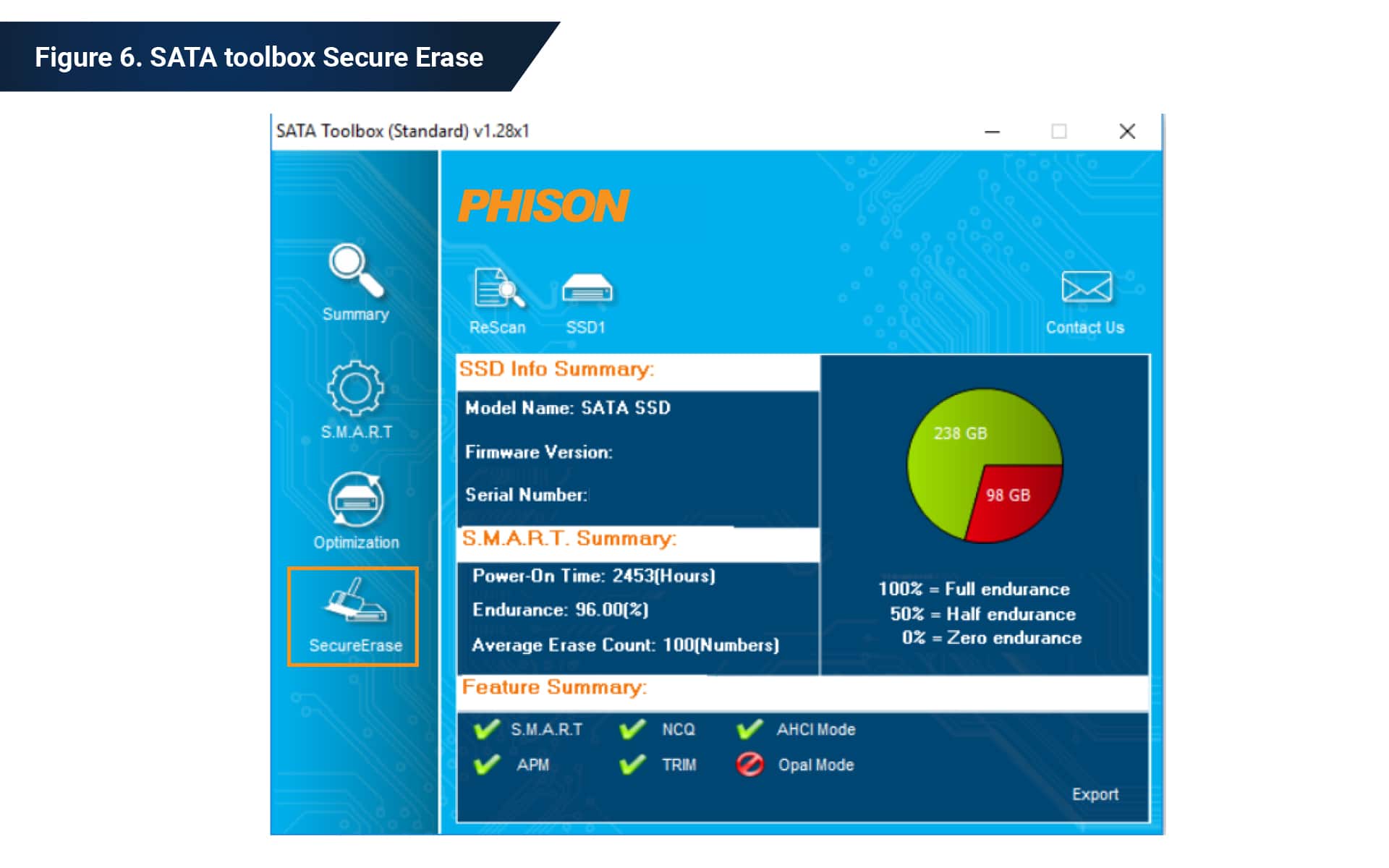
Phison SATA Toolbox supports the secure erase feature
This Windows-based tool is available through your sales contact and can be used to issue the secure erase operation to a Phison SSD drive.
Phison secure erase you can trust
Protecting your company’s data is crucial. Your SSD should not compromise security during active use or after it has been repurposed. The Phison SATA SSD products support an industry-approved secure erase method. By using the Phison Toolbox Secure Erase feature, you can feel confident using Phison SATA SSDs to store your confidential information and keep that information secure.